It allows to keep PV going, with more focus towards AI, but keeping be one of the few truly independent places.
-
The bug allows everyday programs to "illegally" access certain contents in protected kernel memory. The "fix", so to speak, is to implement Kernel Page Table Isolation (PTI), which, for all intents and purposes, makes the kernel invisible to running processes. In a perfect world, such training wheels shouldn't be needed to isolate the kernel, but software patches that are nearing release for Windows, Linux and macOS systems will address the exploit head-on.
Fixing this vulnerability in software also comes with a big hit on performance. Additional overhead is introduced to maintain a barrier between memory address spaces, which can result in a performance handicap of 30 percent or more. However, recent Intel processors with PCID (Process-Context Identifiers) enabled could have the performance impact lessened somewhat.
Both Microsoft Azure and Amazon Web Services have scheduled maintenance that will take place over the next week, although there is no detailed explanation for the downtime.
AMD processors aren't affected by the bug due to security protections that the company has in place.
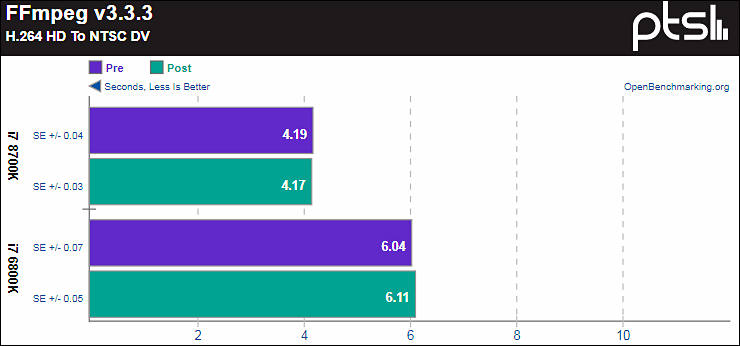
Note - FFmpeg here is joke with almost only CPU load.
Biggest hit can happen with 4K and up raw projects and applications where big amount of data is moved from GPU and back.
Most hit will be for old CPUs, surprise.
Looks like planned thing to save industry after they hit the wall.
https://hothardware.com/news/intel-cpu-bug-kernel-memory-isolation-linux-windows-macos

 sa1216.jpg740 x 346 - 34K
sa1216.jpg740 x 346 - 34K
 sa1217.jpg746 x 352 - 42K
sa1217.jpg746 x 352 - 42K -
Looks like processors back to 2008 are affected...
...still, maybe its all a hoax to deliberitly slow down all old system, so that we all have to buy new ones?
(Or at least we are all forced to upgrade to the latest OS.)
-
It is a privilege escalation attack against hypervisors
Virtual machines and cloud providers will be most affected by the security problem and resulting performance hits.
More info at
http://pythonsweetness.tumblr.com/post/169166980422/the-mysterious-case-of-the-linux-page-table
Means that main hit will be also for shared hosting and VPS providers, as performance hits for them will have direct economic consequences.
-
Well, it is not hoax, it will be used to do slowdown as industry needs it also, but this is real.
In reality such mode in consumer system must be optional.
But it seems that no one will care. As usual capitalist will make hundreds of billions of damage saving few millions for themselves.
-
"funny" coincidence that Brian Kranzich sold all his shares except the bare minimum 5 weeks ago
https://www.fool.com/investing/2017/12/19/intels-ceo-just-sold-a-lot-of-stock.aspx
-
Another similar exploit found for AMD and ARM
https://security.googleblog.com/2018/01/todays-cpu-vulnerability-what-you-need.html
-
We're dealing with two serious threats. The first is isolated to #IntelChips, has been dubbed Meltdown, and affects virtually all Intel microprocessors. The patch, called KAISER, will slow performance speeds of processors by as much as 30 percent.
The second issue is a fundamental flaw in processor design approach, dubbed Spectre, which is more difficult to exploit, but affects virtually ALL PROCESSORS ON THE MARKET (Note here: Intel stock went down today but Spectre affects AMD and ARM too), and has NO FIX.
Spectre will require a complete re-architecture of the way processors are designed and the threats posed will be with us for an entire hardware lifecycle, likely the next decade.
For the past decade, processors were designed to gain every performance advantage. In the process, chipmakers failed to ask basic questions about whether their design was secure.
Meltdown and Spectre show that it is possible for attackers to exploit these design flaws to access the entire memory contents of a machine. The most visceral attack scenario is an attacker who rents 5 minutes of time from an Amazon/Google/Microsoft cloud server and steals data from other customers renting space on that same Amazon/Google/Microsoft cloud server, then marches onto another cloud server to repeat the attack, stealing untold volumes of data (SSL keys, passwords, logins, files etc) in the process.
Intel is not surprisingly trying to downplay the threat of these attacks, but proof-of-concept attacks are already popping up online today, and the timeline for a full rollout of the patch is not clear.
The flaws were originally discovered last June by a researcher at Google Project Zero (shout out @ Jann Horn) and then separately by Paul Kocher and a crew of highly impressive researchers at Rambus and academic institutions. Originally public disclosure was set for next week.
But news of Meltdown started to leak out yesterday, so the disclosure was moved up a week to right now.
-
It is all fine.
But timing coincidence is too good.
My take is that it was VERY LONG known how to use specific CPU stuff for breaking sandboxes.
We now see two main engineering holes controllably leaked using full PR machine.
One is intended to help Intel due to 10nm disaster.
Another is intended to help smartphone vendors as problems on this market started to arise. And this industry will be one that will be hit hardest as nm wall will be hit, for now they just plan to use fake 10nm stuff).
Second one is more important this is why it was leaked with specific delay and masked, as most PR will used later.
-
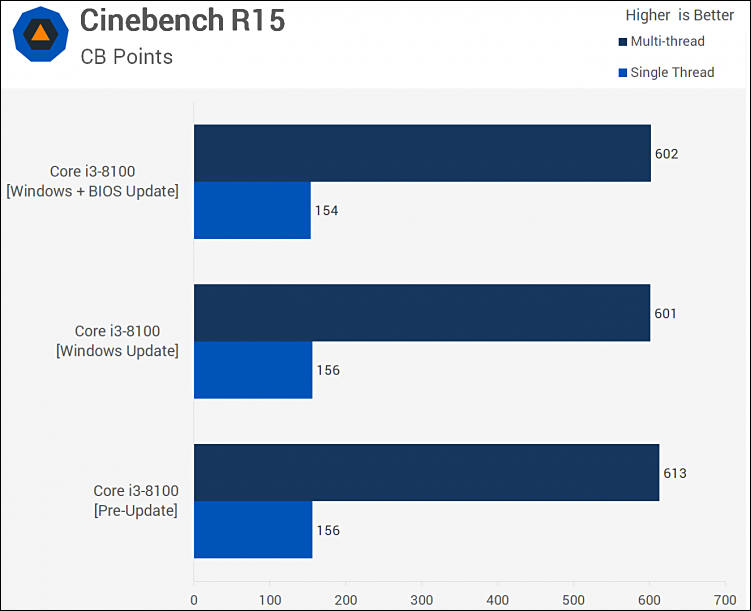
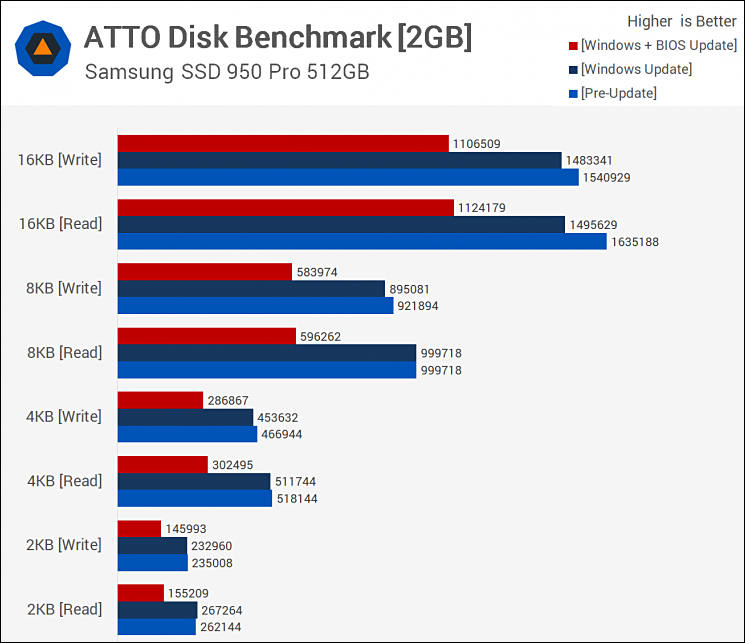
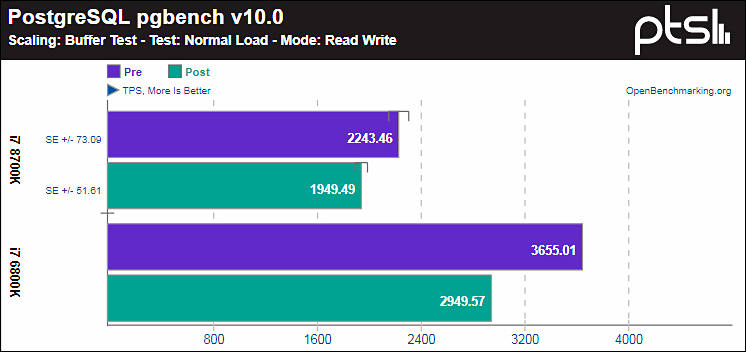
Some tests before and after patch
https://www.guru3d.com/articles-pages/windows-vulnerability-cpu-meltdown-patch-benchmarked.html
-
Most of common tests actually apply bad to real video editing.
Issue is as follows - after patch OS flush cache with each system call and/or also mapping of kernel functions to user space is absent.
Worst affected applications are databases and similar.
Video editors behavior will vary.
Also note that even keeping or decreasing speed 3-5% CPU now heats up significantly more in heavy tasks due to cash flushes. Temperature rise can reach 15%.
As for Spectre - https://spectreattack.com/spectre.pdf it can have more consequences and require huge amount of software fixing. I mean each software, not OS.
Spectre sample code - https://gist.github.com/ErikAugust/724d4a969fb2c6ae1bbd7b2a9e3d4bb6
-
Man, I'm really burned about this. They should replace my chips. $$$.
-
You can check some description (I'll make second part also) at
https://www.personal-view.com/talks/discussion/18660/meltdown-cpu-bug-for-dummies#Item_1
And no one will be replacing you anything.
-
I hope this patches will not apply through OS updates, if we wont update Intels them self we still OK in both windows and macs. am I correct?
-
Meltdown will be patched on OS level.
Spectre family will never be patched completely, as it requires complex applications modifications.
Also new variants can arise. -
So the "solution" for now is keep current OS'es for a good performance without any future updates...even macs. Pity as there is no Intel Coffee Lake support in Mac yet. Theoretically when they came performance will be even to my current not patched workstation (even few year old) :)
There was no reason to upgrades since few years due to lack of noticeable improvements and Intel Coffee Lake seems to be worth it but it will be "patched" as well already. Am I correct?
Conclusion. Verygood no point to span many for upgrades for another while :)
-
So the "solution" for now is keep current OS'es for a good performance without any future updates...even macs. Pity as there is no Intel Coffee Lake support in Mac yet. Theoretically when they came performance will be even to my current not patched workstation (even few year old) :)
If you install any software, load any external word files or browse internet you should use patches for Meltdown.
May be not right now, but after all issues will become known.
-
Some history of thing
Show quite good how big number of people can keep their mouth shut. And it is hundreds of other big stuff things that they will never tell you.
-
Google had to gather hundreds of engineers working across the company to find a way to protect its products. After a few months, they found a solution for Meltdown and the first variant of Spectre (two of the three vulnerabilities), which they then started rolling out way back in September.
So actually information leak was huge long time ago.
Also practice where all but select companies have access to such data is surely illegal.
Howdy, Stranger!
It looks like you're new here. If you want to get involved, click one of these buttons!
Categories
- Topics List24,067
- Blog5,725
- General and News1,391
- Hacks and Patches1,153
- ↳ Top Settings33
- ↳ Beginners256
- ↳ Archives402
- ↳ Hacks News and Development56
- Cameras2,390
- ↳ Panasonic995
- ↳ Canon118
- ↳ Sony156
- ↳ Nikon96
- ↳ Pentax and Samsung70
- ↳ Olympus and Fujifilm102
- ↳ Compacts and Camcorders300
- ↳ Smartphones for video97
- ↳ Pro Video Cameras191
- ↳ BlackMagic and other raw cameras138
- Skill1,960
- ↳ Business and distribution66
- ↳ Preparation, scripts and legal38
- ↳ Art149
- ↳ Import, Convert, Exporting291
- ↳ Editors191
- ↳ Effects and stunts115
- ↳ Color grading197
- ↳ Sound and Music280
- ↳ Lighting96
- ↳ Software and storage tips266
- Gear5,420
- ↳ Filters, Adapters, Matte boxes344
- ↳ Lenses1,582
- ↳ Follow focus and gears93
- ↳ Sound499
- ↳ Lighting gear314
- ↳ Camera movement230
- ↳ Gimbals and copters302
- ↳ Rigs and related stuff273
- ↳ Power solutions83
- ↳ Monitors and viewfinders340
- ↳ Tripods and fluid heads139
- ↳ Storage286
- ↳ Computers and studio gear560
- ↳ VR and 3D248
- Showcase1,859
- Marketplace2,834
- Offtopic1,335