
-
Watching a conversation with Julian Assange, Jacob Appelbaum, Andy Mueller-Maguhn and Jeremie Zimmermann on RT.COM
http://assange.rt.com/cypher-punks-episode-eight-pt1/ http://assange.rt.com/cypherpunks-episode-eight-pt2/
about how governments and corporations spying everything what we are doing and this incredible war which is going on, I was worried and I was immediately inspired to take some concrete action.
1) I installed the Tor-Browser-Bundle https://www.torproject.org/projects/torbrowser.html.en which enables you to surf anonymously in the internet . It is based on Vidalia, Mozilla and Tor-Button.
“The Tor software protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world: it prevents somebody watching your Internet connection from learning what sites you visit, it prevents the sites you visit from learning your physical location, and it lets you access sites which are blocked.”
2) I also installed the Tor-Mail, same idea, anonymous mailing
3) I changed my searching machine to DuckDuck Go, same idea, anonymous searching
I was frightened by the words of Michael Chertoff, 4 years of Bush Administration in Homeland Security and now in charge of Cyber-Security with Obama, when he said in an Al Jazeera documentary called “Cyberwar”: http://www.youtube.com/watch?feature=player_embedded&v=ciAqopNRL0U
“… clearly for certain kinds of interaction you need to know who you are dealing with, and people who are not willing to verify their identity, will simply be refused in minutes.”
“Historically the internet was anonymous – this will have to change.”
“It is dangerous out there… new weapons must be invented”.
It is a frightening scenario. It all looks to me like the US are targeting their next war/fear/economy- syndrome to prepare the ground for their new “war”. They want to control this war and get prepared for this new market. 40-50 Billions are ready to be invested in this area of “cyber-security” – a huge privat sector is waiting to make a lot of money.
I would like to share my concerns, I think it is a very worrying and urgent matter.
And also, is it any useful to install all these Tor applications?
-
Thanks for the Tor browser link. [Edit] I just installed the Linux_64 version, see pic]
Hey, I don't think we have to go and build up some sort of case for privacy here; I have mostly nerdy friends & half of them have given up on retaining privacy. Some say naively, "I've got nothing to hide so I've got nothing to fear"; other non-nerds like my Gen-X daughter have adopted that half-baked "who's got the time to go through all my cat pictures" philosophy.
Some of us just see no reason to trust everybody. Funny, I was just reading "Defensive Computing" at http://blogs.computerworld.com/blog/defensive-computing .
-On the other hand, once I start deliberately sleuth-surfing I am aware that paedophiles and IT-criminals [Edit: and terrorists] are even more likely to want the privacy that I want - and I'm not sure I want to be in that company.
An interesting, topical thread. I hope it gets legs.
 Vidalia.png800 x 481 - 214K
Vidalia.png800 x 481 - 214K -
@Roberto Here is a really interesting presentation by Jacob Appelbaum at a Linux-Meeting in Australia about this whole discussion:
, at approx 12.30min he talks exactly about those who say “we have nothing to hide”, which I think is just a very naive point of view, if you consider that companies such as google, facebook etc. make so much money passing our private information to governments and corporations. Its not only about using all your stored private information against you, it’s also using it to make huge profits.I think if you work continuously with the internet you must develope a precise consciousness about what you are doing “out there”, what data you are ready to share with others or how you can protect yourself now and for the future.
I think times are over when you can just open a browser and start to surf no matter where you end.
-
It's nice to see that the discussion has moved on apace.
you must develop a precise consciousness about what you are doing “out there”
I get the point. If you're preaching to the converted, I'd say we [converted] are the only people worth talking to - and indeed, we don't need any convincing but rather precise and evolving roadmaps about how to behave.
It's very, very strange that this kind of caution is not yet considered a mainstream practice.
-
A useful site with tests you can perform on your own browser history: http://wtikay.com/docs/details.html
-
Mobile phone users sorely mistaken about how much privacy they have
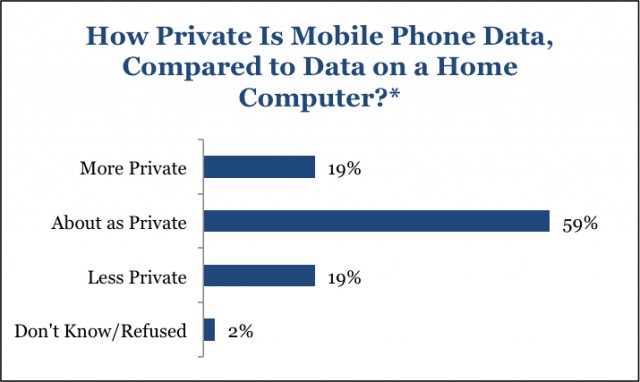
"We found that Americans overwhelmingly consider information stored on their mobile phones to be private—at least as private as information stored on their home computers," states the study, which used information collected by both landline and wireless phones. Fifty-nine percent of all respondents ages 18 to 65 and beyond said their phones were "at least as private" as their home computers, and 19 thought their phones were more private than their home computers.
-
Thanks for that gentle reminder - (I think we were all trying to pretend that can't happen).
It's worse in Aus. Most states have fairly lazy legislation providing respective Police Depts to just ask for ISP records as part of the process of "establishing identity."
(Which makes browser anonymity like TOR about as useful as an ash tray on a motorcycle).
Incidentally, new "consorting" legislation to counter m/c gangs has had its first conviction this month: a mentally handicapped young man was put in jail for shopping with his friends. who had convictions. http://www.sbs.com.au/news/radio/episode/222892/Concern-over-NSW-consorting-law
Facebook friends might well be included...
-
A musician friend works in a sensitive area (not sure exactlly what) but had to go through a long clearance process. As part of this he had a number of very sociable conversations with one of the vetting agents who would then casually ask about all sorts of stuff - musicians he'd played with (my name was mentioned), petitions that had been signed in his name. Things often decades old. Nowadays there's a huge trail available and most people can find out eg the contact details for a website owner without much trouble. I guess the browsing info collected about us is just how we "pay" for access to search services and Internet use generally?
The phone stuff is an eye-opener but I don't use mobiles - never got into them because I lived in a village in the uk which didn't have any mobile service until two years ago.
Howdy, Stranger!
It looks like you're new here. If you want to get involved, click one of these buttons!
Categories
- Topics List23,993
- Blog5,725
- General and News1,354
- Hacks and Patches1,153
- ↳ Top Settings33
- ↳ Beginners256
- ↳ Archives402
- ↳ Hacks News and Development56
- Cameras2,368
- ↳ Panasonic995
- ↳ Canon118
- ↳ Sony156
- ↳ Nikon96
- ↳ Pentax and Samsung70
- ↳ Olympus and Fujifilm102
- ↳ Compacts and Camcorders300
- ↳ Smartphones for video97
- ↳ Pro Video Cameras191
- ↳ BlackMagic and other raw cameras116
- Skill1,960
- ↳ Business and distribution66
- ↳ Preparation, scripts and legal38
- ↳ Art149
- ↳ Import, Convert, Exporting291
- ↳ Editors191
- ↳ Effects and stunts115
- ↳ Color grading197
- ↳ Sound and Music280
- ↳ Lighting96
- ↳ Software and storage tips266
- Gear5,420
- ↳ Filters, Adapters, Matte boxes344
- ↳ Lenses1,582
- ↳ Follow focus and gears93
- ↳ Sound499
- ↳ Lighting gear314
- ↳ Camera movement230
- ↳ Gimbals and copters302
- ↳ Rigs and related stuff273
- ↳ Power solutions83
- ↳ Monitors and viewfinders340
- ↳ Tripods and fluid heads139
- ↳ Storage286
- ↳ Computers and studio gear560
- ↳ VR and 3D248
- Showcase1,859
- Marketplace2,834
- Offtopic1,320





