
-
Canon-related websites that are down include canonusa.com, usa.canon.com, canonhelp.com, imageland.net, consumer.usa.canon.com, cusa.canon.com, and more.
Source shared an image of a company-wide notification titled "Message from IT Service Center" that was sent at approximately 6 AM this morning from Canon's IT department.
This notification states that Canon is experiencing "wide spread system issues affecting multiple applications, Teams, Email, and other systems may not be available at this time."
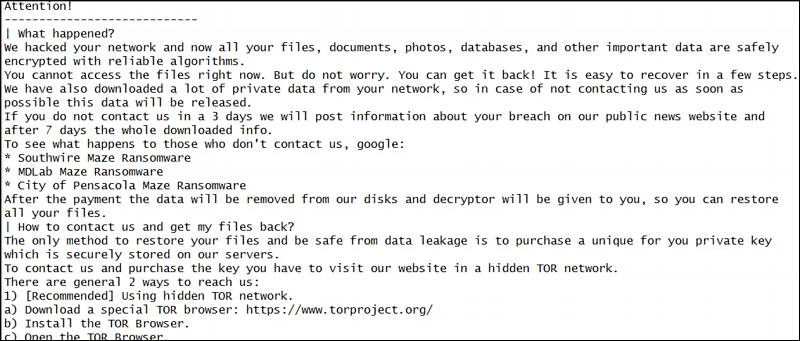
Maze told that their attack was conducted this morning when they stole "10 terabytes of data, private databases etc" as part of the attack on Canon.
If a victim does not pay the ransom, Maze will publicly distribute the victim's stolen files on a data leak site that they have created.
Lets pray that Canon won't play ransom (as Garmin did recently).
This is that happens if you start cutting people without thinking.
-
They are fried like a fish.
-
If some of internal sensitive data will become public it can be huge blow for Canon and also for lot of their ambassadords, influencers and third party reviewers.
Rumors are that hackers got lot of information about present and past PR companies and discussion of reviews preparations and editing process.
-
Rumors in US camera circles is that hackers asked as much as 20 millions USD for first stage only
Reason for such demands are not the sites content, but highly confidential information that they got and that can extremely damage Canon image among photography community.
Garmin paid around 10 millions, but some talk about 35 millions USD via some crypto currencies scheme.
-
Absolutely no progress still.
Canon is expected to pay ransom, but financial sitiation at the company is dire.
I heard at least about one blogger planning to instantly switch field in case of private Canon info opening.
-
Rumors are that Canon paid ransom for part of the data, but largest part is still encrypted.
-
2.2 GB archive called “STRATEGICPLANNINGpart62.zip” was released on the Maze data leak site
Bleeping Computer has been told it contains marketing materials and videos, as well as files related to Canon’s website.
-
Canon understands the importance of protecting information. We are informing current and former employees who were employed by Canon U.S.A., Inc. and certain subsidiaries, predecessors, and affiliates1 from 2005 to 2020 and those employees’ beneficiaries and dependents of an incident that involved some of their information. This notice explains the incident, measures we have taken, and steps you can take in response.
We identified a security incident involving ransomware on August 4, 2020. We immediately began to investigate, a cybersecurity firm was engaged, and measures were taken to address the incident and restore operations. We notified law enforcement and worked to support the investigation. We also implemented additional security measures to further enhance the security of our network.
We determined that there was unauthorized activity on our network between July 20, 2020 and August 6, 2020. During that time, there was unauthorized access to files on our file servers. We completed a careful review of the file servers on November 2, 2020 and determined that there were files that contained information about current and former employees from 2005 to 2020 and their beneficiaries and dependents. The information in the files included the individuals’ names and one or more of the following data elements: Social Security number, driver’s license number or government-issued identification number, financial account number provided to Canon for direct deposit, electronic signature, and date of birth.
We wanted to notify our current and former employees and their beneficiaries and dependents of this incident and to assure them that we take it seriously. As a precaution, we have arranged for them to receive a complimentary membership to Experian’s® IdentityWorksSM credit monitoring service. This product helps detect possible misuse of an individual’s information and provides the individual with identity protection services. IdentityWorksSM is completely free to the individual, and enrolling in this program will not hurt the individual’s credit score. If you are a current or former employee, or the beneficiary or dependent of a current or former employee, and would like more information on IdentityWorksSM, including instructions on how to activate your complimentary membership, please call our dedicated call center for this incident at 1-833-960-3574. For information on additional steps you can take in response, please see the additional information provided below.
We regret that this occurred and apologize for any inconvenience. If you have additional questions, please call 1-833-960-3574, Monday through Friday, between 9:00 a.m. and 6:30 p.m., Eastern Time.
Howdy, Stranger!
It looks like you're new here. If you want to get involved, click one of these buttons!
Categories
- Topics List23,992
- Blog5,725
- General and News1,354
- Hacks and Patches1,153
- ↳ Top Settings33
- ↳ Beginners256
- ↳ Archives402
- ↳ Hacks News and Development56
- Cameras2,367
- ↳ Panasonic995
- ↳ Canon118
- ↳ Sony156
- ↳ Nikon96
- ↳ Pentax and Samsung70
- ↳ Olympus and Fujifilm101
- ↳ Compacts and Camcorders300
- ↳ Smartphones for video97
- ↳ Pro Video Cameras191
- ↳ BlackMagic and other raw cameras116
- Skill1,960
- ↳ Business and distribution66
- ↳ Preparation, scripts and legal38
- ↳ Art149
- ↳ Import, Convert, Exporting291
- ↳ Editors191
- ↳ Effects and stunts115
- ↳ Color grading197
- ↳ Sound and Music280
- ↳ Lighting96
- ↳ Software and storage tips266
- Gear5,420
- ↳ Filters, Adapters, Matte boxes344
- ↳ Lenses1,582
- ↳ Follow focus and gears93
- ↳ Sound499
- ↳ Lighting gear314
- ↳ Camera movement230
- ↳ Gimbals and copters302
- ↳ Rigs and related stuff273
- ↳ Power solutions83
- ↳ Monitors and viewfinders340
- ↳ Tripods and fluid heads139
- ↳ Storage286
- ↳ Computers and studio gear560
- ↳ VR and 3D248
- Showcase1,859
- Marketplace2,834
- Offtopic1,320




