
It allows to keep PV going, with more focus towards AI, but keeping be one of the few truly independent places.
-
Mathy Vanhoef of KU Leuven and Frank Piessens of imec-DistriNet are confident they really have done serious damage to WPA2
According to Iron Group CTO Alex Hudson, disclosure is due some time on Monday, October 16 during European hours.
Info will be at
and

 s1423.jpg442 x 246 - 23K
s1423.jpg442 x 246 - 23K -
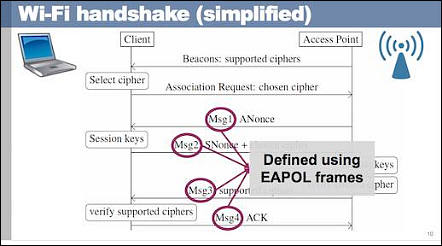
As described in the introduction of the research paper, the idea behind a key reinstallation attack can be summarized as follows. When a client joins a network, it executes the 4-way handshake to negotiate a fresh encryption key. It will install this key after receiving message 3 of the 4-way handshake. Once the key is installed, it will be used to encrypt normal data frames using an encryption protocol. However, because messages may be lost or dropped, the Access Point (AP) will retransmit message 3 if it did not receive an appropriate response as acknowledgment. As a result, the client may receive message 3 multiple times. Each time it receives this message, it will reinstall the same encryption key, and thereby reset the incremental transmit packet number (nonce) and receive replay counter used by the encryption protocol. We show that an attacker can force these nonce resets by collecting and replaying retransmissions of message 3 of the 4-way handshake. By forcing nonce reuse in this manner, the encryption protocol can be attacked, e.g., packets can be replayed, decrypted, and/or forged. The same technique can also be used to attack the group key, PeerKey, TDLS, and fast BSS transition handshake.
If you read it carefully you understand that system was specially designed this way (they have also fun addition about Linux and Android where it is even worse).
Btw whole thing also works only due to artificial encryption weakness.Such security disclosures happens due to some global power things as authors of protocols in need to close some implanted issue to prevent it's usage.
And this year it is 3rd such case.
Howdy, Stranger!
It looks like you're new here. If you want to get involved, click one of these buttons!
Categories
- Topics List23,993
- Blog5,725
- General and News1,355
- Hacks and Patches1,153
- ↳ Top Settings33
- ↳ Beginners256
- ↳ Archives402
- ↳ Hacks News and Development56
- Cameras2,367
- ↳ Panasonic995
- ↳ Canon118
- ↳ Sony156
- ↳ Nikon96
- ↳ Pentax and Samsung70
- ↳ Olympus and Fujifilm101
- ↳ Compacts and Camcorders300
- ↳ Smartphones for video97
- ↳ Pro Video Cameras191
- ↳ BlackMagic and other raw cameras116
- Skill1,960
- ↳ Business and distribution66
- ↳ Preparation, scripts and legal38
- ↳ Art149
- ↳ Import, Convert, Exporting291
- ↳ Editors191
- ↳ Effects and stunts115
- ↳ Color grading197
- ↳ Sound and Music280
- ↳ Lighting96
- ↳ Software and storage tips266
- Gear5,420
- ↳ Filters, Adapters, Matte boxes344
- ↳ Lenses1,582
- ↳ Follow focus and gears93
- ↳ Sound499
- ↳ Lighting gear314
- ↳ Camera movement230
- ↳ Gimbals and copters302
- ↳ Rigs and related stuff273
- ↳ Power solutions83
- ↳ Monitors and viewfinders340
- ↳ Tripods and fluid heads139
- ↳ Storage286
- ↳ Computers and studio gear560
- ↳ VR and 3D248
- Showcase1,859
- Marketplace2,834
- Offtopic1,320




